windows-10-end-of-life-eol-how-to-prepare

Windows 10 End of Life: A Heads-Up for Everyone Windows 10 is heading toward its end of support sooner than many folks expected. If you are still running this operating system and you have a few concerns swimming around in your mind, relax. We are here to walk you through the details, answer common questions, […]
What Is the Role of Cloud Computing in Managed IT Services? Essential Insights for SMBs
A managed IT service provider (MSP) offers end-to-end support for cloud technologies, helping businesses migrate and maintain critical systems. Gain efficiency, tighten security, and elevate productivity with a strategic cloud partner.
Can Managed IT Support Save My Business Money?
Can a business save money by moving some or all IT support functions out-of-house? In many cases, the answer is yes. According to a recent 2025 IT Trends report from CompTIA, companies of all sizes increasingly rely on managed IT support for governance, help desk, and software management to do more with less. Offloading these […]
Are Common MSP Problems Forcing Companies to Switch IT Providers?
Frustrated with your MSP? We spotlight major problems—system failures, slow support, compliance gaps, and missing IT strategy—that cause businesses to switch.
Have You Thought About What an Outage Could Cost Your Business?
Learn how much an outage could cost your business and discover key BC/DR strategies—like backups, redundant internet, and hosted VoIP—to keep you online.
What Are Managed IT Services?
Discover how managed IT services support businesses with proactive monitoring, cybersecurity, cloud management, and more. Find out if they’re right for you.
How Can Managed IT Services Improve My Business Security?
What Are Managed IT Services? A Complete Guide for SMBs Picture this: your business is growing, but your IT headaches keep multiplying. The demands of cybersecurity, data management, and software updates can feel never-ending, leaving you worried about costly downtime or potential breaches. What if you could offload all those headaches—and still retain control? The […]
How Do I Manage the Windows 10 End-of-Life at My Company?
Windows 10 support ends Oct. 14, 2025. Discover what this means for your business, how to transition to Windows 11, and why planning now is crucial.
What Are Best Practices for Managing IT Projects?
Learn how to manage IT projects effectively with clear objectives, strong teams, proactive risk management, and more. Explore best practices for successful outcomes.
What Is the Managed IT Services Onboarding Process Like?
Learn the essential phases of managed IT services onboarding—initial consultation, assessments, clear communication, and more—and why it matters for a smooth, secure transition.
Cybersecurity: Why Businesses Trust Managed Security Service Providers
Discover how managed security service providers help organizations protect data, lower costs, and enable growth. Learn about essential tools, strategies, and the ROI of robust cybersecurity. Get started today!
Define Network Security: Protect Your Business with Business IT Corps
Learn what “define network security” means and how Business IT Corps safeguards your organization through robust cybersecurity strategies, proactive monitoring, and managed IT services.
Managed IT Services in East Texas | Business IT Corps
Discover reliable and cost-effective managed IT services in East Texas from Business IT Corps. Protect your business with 24/7 support, cybersecurity, and custom solutions.
Managed IT Services in Tyler | Boost Security & Productivity
Managed IT Services in Tyler | Boost Security & Productivity What Exactly Are Managed IT Services? Managed IT services involve partnering with an external provider to handle a range of technology-related tasks on your behalf, such as: Network Management – Keep your business connected with a secure, dependable network. Cybersecurity – Stay ahead of online […]
Cybersecurity Risk Management: Protecting Sulphur Springs Businesses

In an increasingly digital world, cybersecurity is a top priority for businesses of all sizes. For businesses in Sulphur Springs, effective cybersecurity risk management is essential to protect sensitive data, maintain customer trust, and ensure business continuity. This blog post will explore the importance of cybersecurity risk management and provide practical strategies for safeguarding your […]
View Google calendar in Outlook
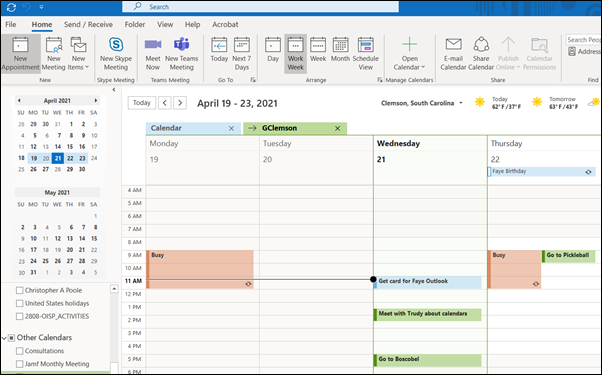
These steps will enable users to see both their Google calendar and Microsoft Exchange calendar together in Outlook. Although these instructions are tailored for Microsoft 365 version 2008, they should be similar for other versions of Outlook. This can be particularly useful for students or individuals with Android phones who want to access their phone’s […]
Data Protection: Understanding Data In Transit vs. Data At Rest

In today’s data-driven world, where information is constantly flowing, the concepts of data in transit and data at rest play a crucial role in ensuring the security and integrity of sensitive data. But what exactly are these terms, and why are they important? Imagine this: you’re sending a confidential email from your computer to a […]
Mastering Network Security: A Complete Policy and Protocol Guide

Is your network security up to par? In an increasingly digital landscape, protecting your network from unauthorized access and potential threats is more crucial than ever. But where do you begin? How do you create effective network security policies and protocols that ensure the safety of your sensitive information? Welcome to our blog, “Mastering Network […]
What is an example of a management service provider?
Advanced Management Strategies for Growing Businesses Technology grows more sophisticated every day. As it does, companies of every size seek ways to keep their operations running smoothly while protecting sensitive data. Management Service Providers (MSPs) respond to this need by offering critical IT support and expertise, enabling internal teams to focus on what truly matters: […]
What is the purpose of MSP?

Introduction In today’s hyper-connected world, businesses need more than just a reliable IT department. They require comprehensive, round-the-clock support to maintain, enhance, and protect their technological resources. Enter Managed Service Providers (MSP), the unsung heroes of modern business operations. But what exactly is the role of MSPs? Let’s dive into the purpose of Managed Service […]
What is managed service provider?

Introduction In an era where digital transformation is no longer an option but a necessity, businesses are increasingly turning to managed service providers (MSPs) to meet their IT needs. But, what exactly is a managed service provider, and how can it benefit your business? Let’s delve into the world of MSPs and discover how they […]
What Is Network Security?

Understanding the Foundations of Network Security Modern businesses thrive on connectivity. Employees, customers, and partners all rely on secure channels to access information. This reliance on technology brings convenience and efficiency, but it also creates avenues for cybercriminals to exploit. Network security represents the structured process of safeguarding networks from unauthorized access, data theft, and […]
What is Cyber Security?

Table of Contents Introduction What is Cyber Security? The Importance of Cyber Security Best Practices for Cyber Security 1. Strong and Unique Passwords 2. Two-Factor Authentication 3. Regular Software Updates 4. Beware of Phishing Attempts 5. Secure Your Wi-Fi Network 6. Regular Data Backups 7. Stay Informed and Educated Conclusion Introduction In today’s interconnected […]
Do you know cybersecurity threats and how to mitigate?

Image Source: FreeImages In today’s digital age, cybersecurity threats are becoming increasingly prevalent and sophisticated. From data breaches to ransomware attacks, organizations and individuals alike are at risk of falling victim to cybercrime. To navigate this ever-evolving landscape, it is crucial to understand the nature of these threats and take proactive measures to […]
How to Create a Cybersecurity Disaster Recovery Plan
Introduction In today’s digital age, cybersecurity is of utmost importance to protect businesses from potential threats and disasters. One crucial aspect of cybersecurity is having a well-defined disaster recovery plan in place. In this blog post, we will discuss the steps involved in creating a cybersecurity disaster recovery plan, while highlighting the expertise of Business […]
What is disaster recovery in cyber security?

In today’s digital landscape, organizations face a constant threat of cyber attacks and breaches. In such an environment, disaster recovery in cyber security plays a pivotal role in safeguarding businesses from potential disasters and minimizing the impact of security incidents. Disaster recovery in cyber security refers to the process of restoring systems, data, and […]
